Introduction: In a dramatic comeback as the first former United States president to be convicted of a felony (unprecedented 34 counts) and re-elected president, President Donald Trump has been firing from all cylinders and following through on his MAGA (Make America Great Again) campaign mantra. Like the proverbial bull in a China shop, his slew of executive orders and protectionist trade wars, imposing a hefty 25% tariff on imports from Canada and Mexico, and 10% on imports from China, is causing panic and economic disruptions around the world. Canada and Mexico retaliated almost immediately while Beijing escalated the trade war by imposing a 15% tariff on coal and liquefied natural gas (LNG), including a 10% tariff on crude oil, agricultural machinery, and certain vehicles from the United States. China also announced a wide range of measures targeting U.S. businesses and launched an anti-monopoly investigation against tech giant - Google (GOOGL.O).
Don Okereke's Blog
Security and Situational Awareness, Open Source Intelligence, Cybersafety and Cybersecurity, Threat Alerts, Geopolitical Risks, etc. Vanguard Of A Countering Violent Extremism Advocacy: "Nigerians Unite Against Insecurity, Terrorism and Insurgency". For Articles, Press Releases, Adverts etc, Email: donnuait(a)yahoo.com, Twitter: @DonOkereke.
Friday, 7 February 2025
The Butterfly-Effect of Trump 2.0 on Geopolitics, Economy And Africa Security
Monday, 20 March 2023
The National Security, Cyber Risks, Geopolitical, Career, Educational Implications of Artificial Intelligence’ – ChatGPT
Introduction: Artificial intelligence (AI) refers to the simulation of human intelligence in machines or
computer systems that are programmed to think like humans and mimic their
actions. Similarly, ChatGPT (Chat Generative Pre-trained Transformer) is an online
artificial intelligence chatbot that is trained to have human-like
conversations and generate detailed responses to queries or questions. ChatGPT became
a blockbuster and a global sensation when it was released in November 2022. According
to web traffic data from similarweb.com, OpenAI’s ChatGPT surpassed one billion page
visits in February 2023, cementing its position as the fastest-growing App
in history. In contrast, it took TikTok about nine months after its global launch to reach 100
million users, while Instagram took more than two years. Users of
ChatGPT span the world, with the United States having the highest number of
users, accounting for 15.73% of the total. India is second with 7.10%. China is
20th with 16.58%, Nigeria is 24th with 12.24% while South
Africa is 41st with 12.63%, as at March 14, 2023. OpenAI, the parent company of ChatGPT is currently valued at about $29 billion. Feedback and reactions from
academics, global
and business leaders to artificial intelligence tools like ChatGPT, is mixed. The likes of Bill Gates agree that ChatGPT can
free up time in workers lives by making employees more efficient. A research titled – ‘’Experimental Evidence on the Productivity
Effects of Generative Artificial Intelligence’’ - by two economics PhD
candidates at the Massachusetts Institute of Technology (MIT) attests that using
ChatGPT made white collar work swifter with no sacrifice in quality and then
made it easier to “improve work quickly”. Israeli president, Isaac Herzog, recently revealed that the opening
part of his speech was written by artificial intelligence software -ChatGPT.
Lately, Bill Gates and the UK Prime Minister Rishi Sunak, were reportedly grilled by AI
ChatGPT during an interview. Similarly, the United States Department of Defense
(DoD) enlisted ChatGPT to write a
press release about a new task force exploiting novel ways to forestall the
threat of unmanned aerial systems. On the flip side, Elon Musk, is of the
opinion that ‘’artificial intelligence is the real existential risk to humankind''. According to
Musk, ''artificial intelligence will
outsmart humanity and overtake human civilization in less than five years’’.
On March 29, 2023, an open letter with signatures
from a bevy of 1,000 prominent tech leaders and researchers from academic and
industrial heavyweights like Oxford, Cambridge, Stanford, Caltech, Columbia,
Google, Microsoft and Amazon, including Elon Musk, Apple co-founder Steve
Wozniak, surfaced online, urging the world’s leading artificial intelligence
labs to pause the training of new super-powerful systems for six months, saying
that recent advances in AI present “profound risks to society and humanity''. Prior to now, theoretical
physicist and one of
Britain's
pre-eminent scientists, Professor Stephen Hawking, seem to agree with Elon Musk.
He warned in in 2014 that
artificial intelligence could spell the end of the human race. In the words of
Hawking, "Once humans develop artificial intelligence it would take off on
its own, and re-design itself at an ever increasing rate’’. He went further to
asset that, ‘’Humans, who are limited by slow biological evolution, couldn't compete,
and would be superseded’’. Cybersecurity experts from the National Cyber
Security Centre (NCSC), a branch of the United Kingdom’s Spy agency, Government
Communications Headquarters (GCHQ), says artificially
intelligent chatbots like ChatGPT pose a security threat because sensitive
queries, including potentially user-identifiable information could be hacked or
leaked.
Monday, 6 February 2023
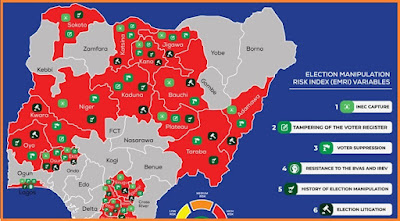
Election Security Risk Analysis: Hybrid Threats, Early Warning Signs And Prospects of A Seamless Political Transition in Nigeria
Thursday, 19 January 2023
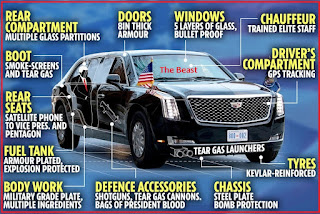
VIP Protection: Advocating For Mandatory Bullet-Proof Vehicle For Armed Police Escort
Introduction: According to the Nigeria Security Tracker, NST, a project of the Council on Foreign Relations’ Africa programme that tracks and maps violence in Nigeria, no fewer than 8,058 lives were cut short violently across Nigeria in 2022. Specifically, no fewer than 138 policemen were killed across Nigeria in the last eight months – January to August, 2022. ‘’States with the highest number of policemen killed within this period are Niger with 24, Enugu with 18, Anambra with 13, Imo 12, Borno and Kogi with nine each. Others include Delta and Kastina with 7 each, Kebbi with 5, Ebonyi and Benue with 4, Cross River, Edo, Oyo, Taraba with 3 each, Jigawa, Rivers, Bayelsa and Ondo with 2 each, Nasarawa, Kaduna, Kwara, Lagos, Osun and the FCT with 1 each’’. The unrelenting and unfolding security challenges in Nigeria seem to have boosted the demand for armed protection services, close or VIP protection, with attendant up-tick in the sale of armoured, bullet proof, reinforced, or treated vehicles. Perhaps this is why Senator Shehu Sani describes bullet-proof vehicles ‘’as a major lifeline in the face of rising insecurity in Nigeria’’. Report by Punch Newspaper, September 26, 2022, shows that as preparations for the 2023 general elections gain momentum and amidst worsening insecurity across the country, the demand for bullet-proof Sports Utility Vehicles in Nigeria have increased significantly. According to Colonel Hassan Stan-Labo (retd.), ‘’politicians were rushing to purchase bullet-proof vehicles because they are very vulnerable, having failed to use public resources judiciously’’. Recall that the use of bullet proof vehicles in Nigeria is regulated by the Office of the National Security Adviser (ONSA). This means that an end user certificate (EUC) is needed and granted to private individuals who provide evidence of threat to their lives. Again, like many paper-tiger stipulations in Nigeria, aforesaid is far from been a hard-and-fast rule.
Tuesday, 3 January 2023
Re: ‘’Abducted officer not yet rescued; search effort ongoing – Nigerian Army’’
Setting The Record Straight
Our attention has been brought to an erroneous and misleading press release on published on Guardian Newspaper, December 31, 2022 and on other
media platforms by the Nigerian Army spokesman, Brigadier General Onyema Nwachukwu
claiming inter-alia, that ‘’Lieutenant PP Johnson, a female army officer, was
abducted on Monday, December 26, 2022, while visiting her grandmother in
Aku-Okigwe in Imo State, shortly after completion of her Cadet training and
subsequent commissioning as a Lieutenant into the Nigerian Army’’.
Apparently, it was on the strength of this false notion that a horde of military personnel and other security agents invaded Aku community in Okigwe LGA on Friday, December 30, 2022, tenably in search of the abducted officer. Reports indicate that rampaging security agents not only shot indiscriminately but plundered, burnt several houses in the hitherto serene Aku community, located in Okigwe LGA of Imo state.
Friday, 9 September 2022
Deteriorating Security at Murtala Muhammed International Airport, Lagos
Wednesday, 31 August 2022
The Role of People in Intelligence Gathering And Sharing
This is the text of a webinar presentation delivered by Don Okereke
Introduction:
Thank you for the privilege and opportunity to partake in this webinar and
share my perspective on The Role of People in Intelligence Gathering by shedding light on the
meaning of intelligence and how it can be shared.
Context:
There is no gainsaying
the fact that insecurity – terrorism, KRE, banditry is pervasive in Nigeria and
the country seems to be coming apart at the seams. For the sake of emphasis, according to a
report by SBM intelligence titled “The Economic of Nigeria’s Kidnap Industry”,
between July 2021 and June 2022, no fewer than 3,420 people were abducted
across Nigeria, with 564 others killed in violence associated with abductions.
The report stated that in the same period N6.531
billion was demanded in exchange for the release of captives while N653.7
million was paid as ransom.
The implication of this is
that while legitimate businesses are struggling in Nigeria, kidnap for ransom
and extortion is obviously the fastest growing industry in Nigeria. What is more distressing
is that there seem to be no end in sight unless there is a positive disruption.
The unrelenting security
challenges we have in Nigeria can be described as largely being man-made and
can be blamed on amongst other things, failure of gathering or disseminating intelligence.
Meaning of intelligence?
Intelligence means many
things to many people.
While INTELLIGENCE can be literarily defined as the ‘’ability to learn or understand or to deal with new or trying situations’’, in the context of security, INTELLIGENCE refers to processed, evaluated data that is usually gathered from trusted sources.
People often use the words ‘Information’ and ‘Intelligence’ interchangeably. However, there is a difference between the two.
Differences Between Intelligence and Information
|
INTELLIGENCE |
INFORMATION |
|
|
1.
|
Information or
knowledge that has been processed and logic applied. |
Pieces of raw data |
|
2.
|
Proactive – can
forecast, correlate, offer supposition and direct an investigation/inquiry. |
Passive – data
accepted and stored |
|
3.
|
Not readily
available. |
Ubiquitous; Available everywhere |
Intelligence gathering
methodologies
There are many ways of gathering
intelligence that are often referred to as "intelligence collection
disciplines". They include:
I.
Human Intelligence (HUMINT) is the collection of information from human sources. The collection may
be done openly, as when DSS/FBI agents interview witnesses or suspects, or it
may be done through clandestine or covert means (espionage).

II. Signals Intelligence (SIGINT) refers to electronic transmissions that can be collected by planes,
drones, ground sites, or satellites. Communications Intelligence (COMINT) is a
type of SIGINT and refers to the interception of communications.
III. Imagery Intelligence (IMINT) is sometimes also referred to as photo intelligence (PHOTINT). Similar
to this is Geospatial Intelligence (GEOINT) - analysis and visual
representation of security related activities on the earth.
IV. Measurement and Signatures Intelligence (MASINT) is concerned with weapons capabilities and
industrial activities.
V. Open-Source Intelligence (OSINT) refers to a broad array of information and sources that are generally
available, including information obtained from the media (newspapers, radio,
television, etc.), professional and academic records (papers, conferences,
professional associations, etc.), and public data (government reports,
demographics, hearings, speeches, etc.).
SOCMINT can be harnessed by government or non-state actors, such as private intelligence agencies or marketing companies, in order to gain knowledge about specific individuals, groups, events, or any number of other targets. SOCMINT data available on social media sites can be either open to the public (e.g., Public posts on Facebook or LinkedIn) or private. Private information -such as contents shared with friends circle- cannot be accessed without proper permission from the creator or complying with best practices, adherence to laws.
The Future of Social Media Intelligence
The future of social media intelligence will be largely impacted by Artificial Intelligence (AI). For instance, AI can analyze extensive amounts of data by instantly identifying trending topics and patterns that exist within social conversations.
Threat intelligence
Threat intelligence also known as cyber threat intelligence (CTI), is the process of identifying, analyzing cyber threats and data to better understand threats and deploying solutions specific to the problem found.
Types of threat intelligence - split into three categories:
Strategic threat intelligence: This is typically a high-level analysis designed for non-technical audiences – for example, the board of a company or organisation.
Tactical threat intelligence: This is focused on the immediate future and is designed for a more technically-proficient audience. It identifies simple indicators or elements such as bad IP addresses, known malicious domain names, unusual traffic, log-in red flags, or an increase in file/download requests. Tactical intelligence is the most straightforward form of intelligence to generate and is usually automated.
Operational threat intelligence: Behind every cyber-attack is a 'who', 'why', and 'how'. Operational threat intelligence is designed to answer these questions by studying past cyber-attacks drawing conclusions about intent, timing, and sophistication.
Intelligence Failures – Why do we have intelligence failures?
Occurs for three reasons –
1. Failure to process and analyze information correctly - the invasion of Iraq by the US
was premised on falsified intelligence.
This can be as a
result of:
§ Selective Information or bias
§ Group think or not thinking outside the box.
§ One Track Mind.
§ Over Complicating Matters.
§ Denial or Avoidance
2. Failure to disseminate and share information - there are claims that the Israelis and
other agencies were privy to 9/11 attacks but they may not have shared the
Intel.
Failure to act on intelligence - Intelligence is useless if not followed up with action.
Probable case studies of intelligence failures in Nigeria
I read how a former governor of Enugu state reportedly got Intel of an impending attack on a community. He promptly shared it with Abuja (the police hierarchy) but they dilly dallied in preventing the attack.
Recent attacks in Nigeria such as the following buttresses lax security and intelligence failure:
§ Note that between 2015 and 2022, there were twenty attacks on prison facilities in Nigeria. 2021 had the highest number of incidents in the 7-year period with a total of 7 attacks. Nearly 9,000 inmates were released from the prison breaks and nearly half of them still on the run. This is a threat to national security.
§ Kuje prison break – Tukur
Mamu, the media aide to Kaduna-based Islamic cleric, Sheikh Ahmad Gumi, said he
shared intelligence with the authorities about the Kuje prison attack,
but the intel agencies failed to act (Channels TV News, July 7, 2022).
According to Daily Trust Newspaper (Tuesday 26 July, 2022), the DSS forwarded 44 security reports to the security agencies warning of attacks on the Correctional Facility in Kuje, Abuja and nothing was done.
If the security agencies didn't act on 44 intelligence reports availed to them by their counterpart, the DSS, there's no assurance that an Intel from a private citizen would be put to good use.
§ The Owo Catholic church attack – over 40 people killed. The attackers mounted
surveillance before attacks.
§ The Kaduna-Abuja train attack – Daily Trust Newspaper (March 311, 2022) reports
that intel agencies provided intelligence, but it was not acted on. Some of the
released victims confessed that they were well fed. Means the terrorists
have access to food/meat, possibly from the local market…
§ Kaduna Airport Security breach – 2nd time in 2 years of security breaches around the Kaduna airport
despite being in the centre of Nigerian security forces.
§ Terrorists ambushed Guards Brigade in Abuja – This was sequel to terrorists reporting writing a letter to
the Management of the Nigerian Law School. An
army captain and 2 soldiers were reportedly
killed. According to a November 2021 report by SBM
Intelligence, ''an estimated 337 Nigerian soldiers
have been killed from insurgents’ ambushes since 2019''
§ President Buhari's advance convoy attacked in Katsina – Tuesday, July 5: An advance convoy of President Buhari was ambushed and attacked in his home state Katsina, specifically at Dutsinma, about 152 kilometres from Buhari’s hometown of Daura. It is either the terrorists had advanced information about the convoy’s movement, or it was a random attack.
§ Sometime in July, 2022, terrorists, who
attacked the Abuja-Kaduna train on March 28, threatened to kidnap President Buhari and the Kaduna state governor, Nasir
El-Rufai. If they can ambush the presidential advance convoy, this
threat should not be waved aside.
§ Nigerian Defence Academy Attack: On Tuesday, August 24, 2021, just a year ago, bandits attacked Nigeria's elite military academy, The NDA, killing 2 officers and kidnapped another in a brazen assault on a symbol of the armed forces.
§ March 23, 2020, about 50 soldiers reportedly lost their lives after Boko Haram staged a deadly ambush on a convoy of troops around Alagarno in Yobe State.
§ June 30, 2022, bandits invaded a mining site in Shiroro LGA of Niger state and reportedly killed ''43 people, including 37 Nigerian security personnel''. This is equivalent to wiping out a PLATOON.
Plethora of Government Intelligence agencies in Nigeria
We cannot talk about the ‘’Role of people in Intelligence Gathering And Sharing’’ without citing the ultimate aggregators, beneficiaries, end-users of intelligence, that is, mainstream government security/intelligence agencies.
Nigeria boasts of a mixed bag of government intelligence agencies. They include but not limited to the following:
§ The National intelligence agency (NIA)
§ The Defence intelligence agency (DIA)
§ Department of State services (DSS)
§ Directorate of Military Intelligence (DMI)
§ Nigerian Army Intelligence Corps - NAIC),
§ Nigerian Navy (Naval Intelligence)
§ Nigerian Air force (Directorate of Air
Intelligence)
§ Nigeria Police Force Criminal Investigation
and Intelligence Department (FCIID)
§ Nigeria Security and Civil Defence Corps (Directorate
of Intelligence and Investigation)
§ Nigeria Customs (Customs Intelligent Unit
or CIU)
§ Nigeria Immigration
Service (HQ National Intelligence Unit)
§ the Nigeria Financial Intelligence Unit (NFIU), an arm of the global financial intelligence unit domiciled within the EFCC
Despite the motley security/intelligence agencies in Nigeria with annual budgets running into billions of Naira, why is insecurity - arms proliferation, kidnapping, banditry, terrorism unrelenting in Nigeria?
Challenges of harvesting and disseminating Intelligence in Nigeria
§ Lack of trust and no love lost between government intelligence agencies and citizens: There seem to be lack of trust and no love lost between private citizens and government security and intelligence agencies in Nigeria. This is largely because Nigerian security and intelligence agencies are often skewed towards ‘regime protection’ or doing the bidding of those in power than fighting for the common man. Pervasive incidents of extrajudicial killings which culminated in the ENDSARS civil unrest buttresses this assertion.
§ Lack of Privacy & Confidentiality: If citizens must feel free to share intelligence with the
security agencies, then their privacy and confidentiality must be guaranteed.
And this is where social media is apt in sharing intelligence anonymously.
§
Lack of synergy, Inter agency rivalry and superiority/inferiority
complex: This is
the bane of the security and intelligence agencies in Nigeria. It appears they
are working at cross-purposes.
§ Politics is superior to security, nay,
intelligence in Nigeria: There is a saying that politics is superior to economics. It may be
safe to also submit that politics is superior to security and intelligence in
Nigeria. We understand that politicians seldom dissect or treat nuggets of
intelligence reports made available to them. It can be a tough decision trying
to balance perception or likely panic and trying to be decisive.
Is there anyone here who watched
the BBC Africa Eye video: The Bandit Warlords of Zamfara? The NBC imposed a fine of N5 million on
broadcast platforms that aired the documentary on the grounds that they ‘promoted
terror in the country’. The inference from the documentary is that masterminds
of banditry and terrorism in parts of the country are not invincible after
all. In some climes, government intelligence agencies will synergize with those
makers of the documentary to harvest actionable intelligence from them. It
appears the Nigerian establishment doesn’t appreciate the publicity and feel
embarrassed because they probably had all the intel but have failed to act.
Anyway, the government hates competition… As we
speak, notorious bandit leader, Turji Bello is
said to have been granted an ‘amnesty’ and ‘embraced peace’ in Zamfara state. Imagine
the faith of someone who gave out intelligence about him.
§ Lack of anonymity: Scores of Nigerians don't feel free volunteering
information, nay, intelligence to government security, intelligence agencies.
You don't even know if the person you are giving the information is a
sympathizer. Recall that a Premium
Times January 8, 2012 report quoted former
President Goodluck Jonathan as admitting that members of the extremist Boko
Haram sect succeeded in infiltrating his government,
planting its members in government agencies and security outfits.
§ Food for thought: Why is that more often than not, when the Nigerian government or the security denies anything, it turns out there’s some iota of truth in what they are trying to deny?
How to share intelligence
Intelligence sharing is the process of exchanging actionable
intelligence, information, data, or knowledge amongst relevant government
agencies or private-sector entities as appropriate.
The Bible says Can two walk together without
agreeing where to go? You can only share intelligence or information
if you have a good relationship and mutual trust with the second party.
Intelligence
can be shared amongst the security cum intelligence agencies - inter agency
collaboration. Ideally, Private citizens should also be able to share
intelligence with the security / intelligence agencies. I said ideally
because we know this is not always the case in Nigeria and the reason is not
far-fetched.
Why
private sector, citizens need to be involved in intelligence gathering.
With due
respect, the home truth is that Nigerian Security And intelligence agencies are
overwhelmed, stretched hence they tend to be more reactive than proactive.
Similar to this, they tend to devote more effort to regime protection, stifling
supposed opposition than fighting criminals. I commend the likes of SBM
intelligence, Bulwark Intelligence amongst others and I recommend that Nigerian
intelligence agencies find a way to partner with private companies in the
business of harvesting intelligence.
While some
people may blame mainstream intelligence agencies for the security breaches in
Nigeria, I think we are all complicit. As we say, security is a collective
responsibility.
Gathering or
sharing intelligence is not the exclusive preserve of government
security/intelligence agencies. The democratization of Intelligence
entails that Corporate organizations, private security companies,
security professionals and private citizens are now deeply involved in the
business of intelligence gathering and sharing.
Just like Georges Clemenceau quote that
“War is too important to be left to the
generals”, I can paraphrase this to say that intelligence is too important to be left in the hands of
government intelligence agencies.
§ Social media is the new normal in
intelligence gathering and sharing:
§ Extremist groups such
as Boko Haram/ISWAP, Abuja-Kaduna train kidnap masterminds share videos etc.
online and those videos or images can be geolocated and clues pinpointing
location deducted.
§ It is not encouraging that some government
intelligence agencies in Nigeria seem to be ‘social media shy’. I mean they
don’t have official social media accounts. Granted
operatives of Nigeria’s intelligence agencies, the DSS, NIA, ONSA of this world have social media
accounts and they do follow individuals of interest (especially perceived
dissenters and opposition) on social media, the lack of official presence on
social media means they won’t be able to receive nuggets of intelligence from
citizens, anonymously.
§ This contrast with the practice across the
world where the intelligence agencies are quite active online and can be
reached via social media. For instance, according to the report: ‘’Spy Influencers: Social Media Secrets
of the CIA, MI5, Mossad & More’’, the ‘The FBI reportedly runs more than 70 social media sites!
§ Britain’s domestic intelligence agency, the
Mi5, which is the equivalent of Nigeria’s DSS, officially joined Instagram a
while ago @Mi5official.
§ Canada's Communications
Security Establishment (CSE), the Canadian spy agency has
LinkedIn, Twitter, Instagram, and YouTube accounts.
Nigerian intelligence agencies should take a cue from UK's Mi5, the American FBI etc. by embracing social media. Social media cuts red tape and bureaucracy in sharing intelligence. Imagine if I have an actionable intelligence that I want to share directly with the National Security Adviser. It would be easier if I have his twitter handle. I can also do that anonymously.
See Something, Say Something
Local communities and citizens play an important role in preventing
criminality, terrorism and keeping our communities safe.
The public should report suspicious activity such as the discovery of a
suspicious package or suspicious behavior, such as someone breaking into a
restricted area, attempting to gain access into a restricted area, or making
suspicious purchases of precursor chemicals (like fertilizer, )
Abduction of Umaru Dikko in London: It took the
observance of a private individual to foil the abduction and repatriation of Umaru
Dikko in London On Thursday, July 5, 1984, a team of Nigerian intelligence
and Israeli agents.
According to the Money Laundering Act: Financial institutions and
designated non-financial institutions must report transactions in excess of 5
million Naira for individuals or 10 million Naira for legal persons to the EFCC
within seven days of such transaction taking place. How many financial
institutions actually do this? If they do, they will help in sniffing out
kidnappers and bandits. Following the money is a global
anti-terror and crime-fighting tactic.
Ways to Use OSINT for
Corporate Security
Thanks to the rapid growth of public data, OSINT
has now established itself as an indispensable tool for business risk
management and can be deployed in:
1. Executive
Protection: In early-January 2020, the corporate security
team at Fiserv advised against executive travel to China after initial reports
of COVID-19 disease outbreak weeks before most U.S. companies even acknowledged
COVID-19.
Executive protection details can scan open
sources to spot travel risks, route assessment and emerging events. If they
spot a suspicious post, teams can exploit open source intelligence to gauge the
credibility of a threat. Such situational awareness enables protectors to avoid
dangerous areas, set up alternative travel plans, or respond quickly to
incidents.
2. Protecting
against Operational, brand or reputational risks- OSINT can be used to
monitor Misinformation, fake news or false rumors spreading like wild-fire
online. Such negative publicity could damage a brand, VIP’s reputation, their
ability to conduct business, or the value of the organization they represent.
Keeping tabs on any rumors or false reports allow corporate security teams to
respond quickly.
3. Identifying investment opportunities - OSINT is becoming the new litmus test for investors because it is used for due diligence investigation due to benefits of speed and size. Private equity firms use our OSINT-powered due diligence to know who they’re dealing with, helping lower the risks. For instance, a single tweet or a just published image can be an early signal of a major market event that would completely change the winning strategy regarding particular stocks.
4. OSINT/SOCINT and civil unrest monitoring: Examples are the Capital Hill unrest in the United States, the ENDSARS civil unrest in Nigeria had massive social media footprint in real-time. Similarly, the “Arab Spring” and insurrections in Egypt demonstrates the importance of OSINT/SOCMINT at a strategic level to intelligence tradecraft, as well as the inefficacy of traditional intelligence sources and methodologies.
5. Loss And Fraud Prevention - Retail organizations around the world are fully embracing open source intelligence (OSINT) to filter through billions of online posts to discover valuable intelligence for their security operations, protect assets, detect internal and external fraud and data breaches. Criminal groups often exploit social media to coordinate robberies or share tips and tactics with their fellow thieves.
6. Supply Chain Protection - The process that delivers a product to store shelves is a tightly interconnected network. If one link in that chain fails — from sourcing and manufacturing to transportation — the whole system breaks down. A supply chain disruption can result in millions of dollars of lost sales for retailers, result in financial losses and impair the reputation of the entire company.
7. Event Security - Savvy event managers employ open source intelligence to protect attendees. OSINT can be used to Anticipate Risks and spot potential problems ahead of time. Continuous Intelligence: Security teams often conduct a threat assessment ahead of an event. Locate an Incident: Geo-tagged social media posts allow teams to quickly determine where an incident has taken place.
8. Monitoring Data Leaks and Social Engineering: - The average cost of a data breach for organizations now tops almost $3.9 million, according to a 2021 survey by IBM and increased to $8.2 million on average per incident for companies based in the US.
9. Crisis
Response - Corporate security teams basically contend
with three types of hazards: Natural hazards (floods,
earthquakes, and blizzards); Technological hazards (power
loss, industrial accidents, and infrastructure failures), man-made hazards (October 2020 ENDSARS, January 6, 2021 Capitol attack in the US, cyber-attacks,
terrorist threats, or workplace violence.
Suspicious activity/intelligence worth sharing?
Suspicious activity may include an unusual interest in gaining sensitive
information about a facility security, operations, or maintenance.
§ An unattended bag or backpack.
§ Suspicious purchases of items that could be
used to construct an explosive device, including hydrogen peroxide, acetone,
gasoline, propane, or ammonium nitrate fertilizers.
§ Theft of explosive materials.
§ Theft of security personnel uniforms or
credentials
§ Attempted/unauthorized access to rooftops
or other potentially sensitive areas.
§ Individuals acting suspiciously around the
entrances to an event location.
§ Unusual or bulky clothing that is
inconsistent with the weather.
What information should citizens report?
§ Who or what you saw (specifics)
§ When you saw it (time).
§ Where it occurred (exact
place, landmark)
§ Why or what makes the incident suspicious.
Contact Emergency Numbers –
§ Lagos State Government: 767 and 112.
§
Nationwide: The
Nigeria Police Force recently secured '933' Short Code For Free
Emergency calls and information sharing with the citizens.
Concluding remark:
Remember that security is everyone’s business, If You See Something, Say Something. As we have seen from this presentation, intelligence is not the exclusive preserve of national security. Numerous security lapses, including recurrent jailbreaks, intensifies the exigency to retool Nigeria’s intelligence gathering architecture and boost inter-agency coordination. There is need for real-time information sharing and also need to plug leakages of sensitive information.
Let's hope Nigeria’s newly created and much touted National Counter Terrorism Strategy
Document (NACTEST), National Crisis Management Doctrine (NCMD), and the National
Counter Terrorism Centre (NCTC) domiciled in the of the Office of the National
Security Adviser (ONSA) enhances inter-agency collaboration between the
intelligence agencies and the Nigerian Army, the Nigeria Police Force, the
Nigerian Army, and the Nigerian Airforce, amongst others, at strategic,
operational, and tactical levels.
References:
1.
7 Ways to
Use OSINT for Corporate Security
https://www.liferaftinc.com/blog/7-ways-to-use-osint-for-corporate-security
2.
Open Source Intelligence For Retail Security
Updated February 9,
2021
https://www.echosec.net/blog/open-source-intelligence-for-retail-security
3.
OSINT Tools and Techniques for Business Risk
Intelligence
https://www.echosec.net/blog/osint-tools-and-techniques-for-business-risk-intelligence
4.
OSINT Tools
https://www.osinttechniques.com/osint-tools.html
5.
Managing OSINT Tools
6.
Introducing Open Source Security Management at
Enterprise Scale
Gauthami Polasani
https://fossa.com/blog/introducing-open-source-security-management-at-enterprise-scale/
7.
Understanding OSINT
https://www.triangular-intelligence.com/the-power-of-osint
8.
OSINT Business Data: Actionable Intelligence For
Company Growth
May 27, 2022
https://coresignal.com/blog/osint-business/
9.
OSINT Due Diligence: The New Litmus Test For
Investors
https://www.neotas.com/osint-powered-due-diligence-the-new-litmus-test-for-investors/
10.
6 Open Source Intelligence (OSINT) Applications
for Your Business
https://www.skopenow.com/news/6-open-source-intelligence-osint-applications-for-your-business
11.
Using WEBINT and OSINT to tackle extremist
groups
12.
Producing Actionable Intelligence With OSINT
https://www.companionlink.com/blog/2022/01/producing-actionable-intelligence-with-osint/
13.
How to Leverage OSINT Data During a Crisis
https://store.asisonline.org/how-to-leverage-osint-data-during-a-crisis.html
14.
OSINT Geolocation Guide and Best OSINT
Geolocation Tools
https://www.osintguru.com/blog/geolocation
15. Six Tools To Help With Geolocation
https://nixintel.info/osint-tools/six-tools-to-help-with-geolocation/
16.
Private guard companies recruit over 4.2million
people in 6 years - NBS Monday,
https://www.legit.ng/1219749-private-guard-companies-recruit-42million-people-6-years-nbs.html
17. The economics of Nigeria’s kidnap industry,
an update
https://www.sbmintel.com/2022/08/the-economics-of-nigerias-kidnap-industry-an-update/
18. DSS Presented 44 Security Reports Before
Kuje Attack
https://dailytrust.com/just-in-dss-presented-44-security-reports-before-kuje-attack-wase
19. Between 2015 and 2022, there were twenty attacks on prison facilities in Nigeria.
20.The FBI reportedly
runs more than 70 social media sites!
21. Private guard companies recruit over
4.2million people in 6 years - NBS Monday,
https://www.legit.ng/1219749-private-guard-companies-recruit-42million-people-6-years-nbs.html
22. OSINT Goes Mainstream: How Security Teams
Can Use Open-Source Intelligence To Help Companies Understand Risk
24.
Are spy agencies ready for open-source
intelligence?
25.
MI5 warns of spies using LinkedIn to trick staff
into spilling secrets
https://www.bbc.co.uk/news/technology-56812746
26.Open-Source
Intelligence (OSINT) Use by Governments
https://hackernoon.com/open-source-intelligence-osint-use-by-governments-802t37gn
27. Seven Ways to Use OSINT for Corporate Security
https://www.liferaftinc.com/blog/7-ways-to-use-osint-for-corporate-security
28.The Advantages and Challenges of Utilizing SOCMINT for National Security
Affairs
29.Intelligence Studies: Types of Intelligence Collection
https://usnwc.libguides.com/c.php?g=494120&p=3381426
30.
Social Media Intelligence
https://privacyinternational.org/explainer/55/social-media-intelligence
31. Social media intelligence, the wayward
child of open source intelligence
32. Buhari launches national crisis management
doctrine
https://www.premiumtimesng.com/news/548341-buhari-launches-national-crisis-management-doctrine.html
33. Boko Haram has infiltrated my government, says
Jonathan
https://www.premiumtimesng.com/news/3360-boko-haram-has-infiltrated-my-government-says-jonathan.html
34.Budget: Despite extra N12 trillion in 7 years,
security remains elusive, as education, health suffer
35. NBC imposes N5 million fine on Trust Television
over documentary on banditry
36.
INTELLIGENCE
SHARING: THE CHALLENGES AMONG THE NIGERIAN SECURITY AGENCIES AND GOVERNMENT
37. With NCMD, Police Have Five Minutes To Respond To
Kidnap Attacks – Presidency
38.
National Counter-terrorism Strategy
(NACTEST)
39.
https://www.kaspersky.com/resource-center/definitions/threat-intelligence