 |
| Credit: betanews.com |
People are becoming increasingly concerned about their security. They
use two-step authentication, login alerts, and third-party security
services to better protect their email and social media accounts. One
would hope for a similar -- if not more secure -- level of protection
from our banks. After all, this is the place where we put most of our
earnings and savings. However, apparently we are all mistaken. Mobile
security firm Appvigil is reporting
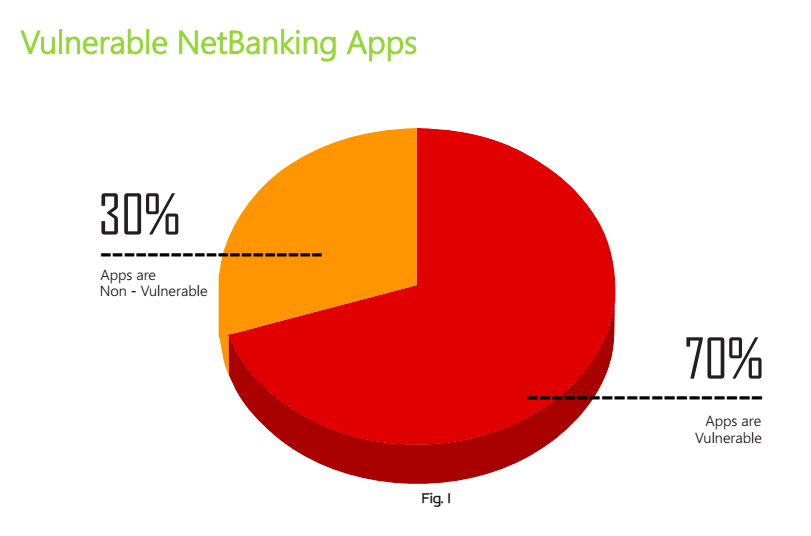
that as many as 70 percent of the top 100 mobile banking apps on the
Android operating system in the APAC region are vulnerable to security
attacks and data leaks.
Don’t live in the said region? That’s no reason
to relax. The report further pinpoints vulnerabilities in mobile banking
apps found in other regions as well.
The security firm tested the mobile banking apps of the top 29 Indian
banks and 71 more in the Asia Pacific region and the results are
staggeringly bad. "Most of the mobile banking apps failed and many
didn’t employ even the basic security checks expected. The communication
between the apps & their servers is still in the unencrypted format
i.e. in HTTP instead of HTTPS", the report reveals.
In the past couple of years as security threats reached new heights,
most of the banks in European and American regions implemented security
measures such as authentication using e-tokens, one-time passwords
(OTP), and confirmation of transactions through codes sent to Android
phones, but as Appvigil points out -- which is in line with news reports
we have seen previously -- cybercriminals have developed tools that
bypass these measures.
"There are numerous ways by which security loopholes can arise in an
Android application. Organizations today, are focusing more on state of
the art features, responsive and performance optimization issues without
paying much heed to security. In most of the cases people react to
security issues only when they face some discrepancies via a malicious
threat agent", the report adds.
Furthermore, the report chalks out loopholes -- such as issues of
system clock accuracy, and time synchronization -- arising due to
ignorance by our carriers and network admins. "If certain processes run
out of sequence, such as transaction processing and backups, then the
results of these processes may cause discrepancies, due to the
transaction times failing to tally. Mismatched timestamps often cause
financial and database program errors".
The firm found a staggering 983 security vulnerabilities in the 100
mobile banking apps it tested. These vulnerabilities include exploits
such as intent spoofing, unintended data leakage, SQL injection,
JavaScript injection, XML injection, and unencrypted sockets among
others. "The findings of our analysis presented in this report have a
different story to tell. It's evident from the report that most of the
apps are vulnerable to security attacks with 82 percent of apps carrying
high severity vulnerabilities in them. On an average, 14 security bugs
per app are present. Surprisingly, we found five mobile banking apps
which had more than 50 security vulnerabilities in each of them". You
can read more about it here.
You should be concerned about this even if you don’t live in the APAC region. Gizmodo did a comprehensive rundown
of existing security measures utilized by all major banks in the United
States and other regions, and the results were woeful. We contacted
AVG, a popular mobile security firm to see what they think about this
report. "There are banking apps in many markets which can be vulnerable
to compromise but we are aware that banks do prioritize working on a fix
obviously", Yuval Ben-Itzhak, CTO at AVG tells BetaNews.
"An example of one of these vulnerabilities is where an app downloads
data and caches it on the device in multiple places. Some of these
files may be able to be accessed by other apps and may not be removed
after the banking app has used them. An uninstaller app would help
ensure such data is removed for security purposes. Another example would
be where an app is using a vulnerable WebView component, such as on a
version of Android that is earlier than 4.1, which may leave it open to
risk.", he added.
Source:
No comments:
Post a Comment