A new report from the U.S. Treasury Department found
that a majority of bank account takeovers by cyberthieves over the past
decade might have been thwarted had affected institutions known to look
for and block transactions coming through Tor, a global communications network that helps users maintain anonymity by obfuscating their true location online.
The findings come in a non-public report obtained by KrebsOnSecurity that was produced by the Financial Crimes Enforcement Network
(FinCEN), a Treasury Department bureau responsible for collecting and
analyzing data about financial transactions to combat domestic and
international money laundering, terrorist financing and other financial
crimes.
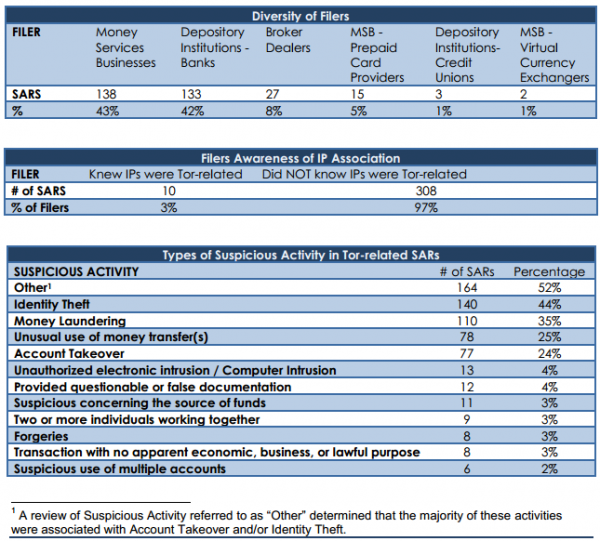
In the report, released on Dec. 2, 2014, FinCEN said it examined some
6,048 suspicious activity reports (SARs) filed by banks between August
2001 and July 2014, searching the reports for those involving one of
more than 6,000 known Tor network nodes. Investigators found 975 hits
corresponding to reports totaling nearly $24 million in likely
fraudulent activity.
“Analysis of these documents found that few filers were aware of the
connection to Tor, that the bulk of these filings were related to
cybercrime, and that Tor related filings were rapidly rising,” the
report concluded. “Our BSA [Bank Secrecy Act] analysis of 6,048 IP addresses associated with the Tor darknet [link
added] found that in the majority of the SAR filings, the underlying
suspicious activity — most frequently account takeovers — might have
been prevented if the filing institution had been aware that their
network was being accessed via Tor IP addresses.”
FinCEN said it was clear from the SAR filings that most financial
institutions were unaware that the IP address where the suspected
fraudulent activity occurred was in fact a Tor node.
“Our analysis of the type of suspicious activity indicates that a
majority of the SARs were filed for account takeover or identity theft,”
the report noted. “In addition, analysis of the SARs filed with the
designation ‘Other revealed that most were filed for ‘Account Takeover,’
and at least five additional SARs were filed incorrectly and should
have been ‘Account Takeover.'”
The government also notes that there has been a fairly recent and
rapid rise in the number of SAR filings over the last year involving
bank fraud tied to Tor nodes.
“From October 2007 to March 2013, filings increased by 50 percent,”
the report observed. “During the most recent period — March 1, 2013 to
July 11, 2014 — filings rose 100 percent.”
While banks may be able to detect and block more fraudulent
transactions by paying closer attention to or outright barring traffic
from Tor nodes, such an approach is unlikely to have a lasting impact on
fraud, said Nicholas Weaver, a researcher at the International Computer Science Institute (ICSI) and at the University of California, Berkeley.
“I’m not surprised by this: Tor is easy for bad actors to use to
isolate their identity,” Weaver said “Yet blocking all Tor will do
little good, because there are many other easy ways for attackers to
hide their source address.”
Earlier this summer, the folks who maintain the Tor Project
identified this problem — that many sites and even ISPs are increasingly
blocking Tor traffic because of its abuse by fraudsters — as an
existential threat to the anonymity network. The organization used this
trend as a rallying cry for Tor users to consider lending their brainpower to help the network thrive in spite of these threats.
A growing number of websites treat users from anonymity services differently Slashdot doesn’t let you post comments over Tor, Wikipedia won’t let you edit over Tor
“A
growing number of websites treat users from anonymity services
differently Slashdot doesn’t let you post comments over Tor, Wikipedia
won’t let you edit over Tor, and Google sometimes gives you a
captcha when you try to search (depending on what other activity they’ve
seen from that exit relay lately),” wrote Tor Project Leader Roger Dingledine. “Some sites like Yelp go further and refuse to even serve pages to Tor users.”
Dingledine continued:
“The result is that the Internet as we know it is siloing. Each
website operator works by itself to figure out how to handle anonymous
users, and generally neither side is happy with the solution. The
problem isn’t limited to just Tor users, since these websites face
basically the same issue with users from open proxies, users from AOL,
users from Africa, etc.
Weaver said the problem of high volumes of fraudulent activity coming
through the Tor Network presents something of a no-win situation for
any website dealing with Tor users.
“If you treat Tor as hostile, you cause collateral damage to real
users, while the scum use many easy workarounds. If you treat Tor as
benign, the scum come flowing through,” Weaver said. “For some sites,
such as Wikipedia, there is perhaps a middle ground. But for banks?
That’s another story.”
Source:
krebsonsecurity

No comments:
Post a Comment